Enabling SOCKS5 Proxy on Windows Tailscale
Introduction
Tailscale is an excellent zero-configuration VPN tool that can easily connect our devices into a secure private network. However, by default, Tailscale takes over some or all of the system’s network traffic (for example, when using Exit Nodes). Sometimes, we may only want certain specific applications (such as browsers, download tools, or command line) to access resources through the Tailscale network, rather than affecting the entire system.
Fortunately, Tailscale provides a powerful feature: Userspace Networking mode, with a built-in SOCKS5 proxy server. By enabling it, we can use Tailscale as a local proxy service, allowing applications to connect on demand, thus achieving more granular and flexible traffic control.
Core Principles
To enable SOCKS5 proxy, we need to modify the startup parameters of the Tailscale Windows service by adding the following two key parameters:
-tun=userspace-networking: This parameter transfers Tailscale’s network processing from kernel space (TUN driver) to user space. This is a prerequisite for enabling the built-in proxy functionality.-socks5-server="127.0.0.1:<port>": This parameter starts a SOCKS5 proxy server listening on the specified local port. Common ports include1080,10800, etc. You can choose according to your needs, just ensure the port is not occupied.
Operation Steps
There are several methods to modify Windows service startup parameters. Here we introduce several commonly used approaches.
Method 1: Using Registry Editor (Recommended)
This is the most direct method that doesn’t require additional tools.
-
Open Registry Editor: Press
Win + R, typeregeditand press Enter. -
Navigate to Tailscale service entry: Paste and navigate to the following path in the address bar:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tailscale -
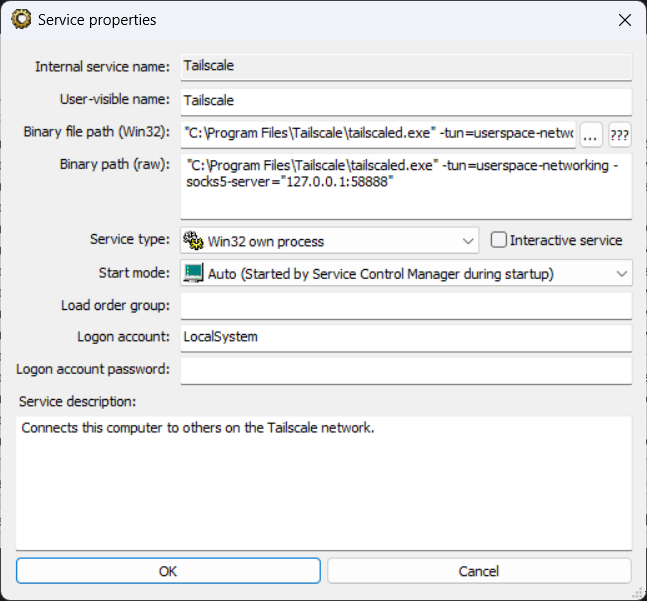
Modify ImagePath value: In the right panel, find the string value named
ImagePathand double-click to open it. Its default value is usually:"C:\Program Files\Tailscale\tailscaled.exe" -
Add startup parameters: At the end of the original value, outside the quotes, add the parameters we need. For example, using port
1080:"C:\Program Files\Tailscale\tailscaled.exe" -tun=userspace-networking -socks5-server=127.0.0.1:1080Note: Please ensure your Tailscale installation path matches the path in
ImagePath. -
Save and close: Click “OK” to save the changes, then close Registry Editor.
Method 2: Using Command Line (Advanced)
For users familiar with command line, you can use the sc (Service Control) command to quickly complete the configuration.
-
Open Command Prompt or PowerShell as administrator.
-
Execute the following command:
sc.exe config Tailscale binPath= "\"C:\Program Files\Tailscale\tailscaled.exe\" -tun=userspace-networking -socks5-server=127.0.0.1:1080"Important Note: There must be a space after
binPath=. The entire path and parameters need to be wrapped in double quotes, and the executable file path itself also needs to be wrapped in escaped double quotes\"to handle spaces in the path.
Method 3: Using Third-party Service Management Tools
If you’re accustomed to using graphical tools to manage services, you can use third-party tools like srvman. The operation logic is consistent with the previous two methods: find the Tailscale service and edit its “executable file path” or “startup parameters” field.
Restart Service and Verify
After completing the configuration modification, you must restart the Tailscale service for the new parameters to take effect.
- Press
Win + R, typeservices.mscand press Enter to open Service Manager. - Find
Tailscalein the service list. - Right-click on it and select “Restart”.
Notes and Advanced Tips
The performance of userspace networking is usually slightly lower than kernel mode because network packets need to be copied between kernel and user space. For most daily applications (web browsing, code synchronization), this difference is almost imperceptible, but it may have an impact in high-throughput scenarios.
Summary
By enabling Tailscale’s userspace networking mode and built-in SOCKS5 proxy, we have successfully transformed a comprehensive VPN tool into a flexible, on-demand network proxy service. This approach not only allows us to precisely control which applications use the Tailscale network, but also provides great convenience for implementing advanced scenarios such as per-application proxy and secure access to internal network resources.
I hope this guide helps you better master Tailscale and unlock more of its potential.